Ensuring GDPR Compliance with AWS

Ensuring compliance with the General Data Protection Regulation (GDPR, or DSGVO in German) is a complex process that requires both technical and organisational measures. At first glance, using a non-European cloud provider to host your services while staying GDPR-compliant may seem challenging. This blog post will clarify the roles and responsibilities of the involved parties, outline the measures AWS users should take to meet GDPR requirements, and explain how evoila can support the secure integration of AWS into an organisation’s IT landscape. The focus lies on technical challenges, as these can be generalised across organisations, whereas organisational measures must be addressed individually
The participating parties, their roles, and duties
To set the scene, let’s simplify things by assuming there are only two parties involved: AWS and you, the AWS customer. Each has different roles and obligations depending on the scenario. Under the GDPR, two key roles are defined – the Data Controller and the Data Processor – both of which are particularly relevant when using AWS.
The Data Controller is the entity (or entities) that determines the purposes and means of processing personal data.
The Data Processor, on the other hand, is the entity that processes personal data on behalf of the Data Controller. Let’s clarify this with an example, which also helps illustrate what qualifies as personal data: Imagine you want to get in touch with us at evoila to explore the use of AWS in your organisation. You enter your email address into the contact form on our website and hit send. In this case, evoila acts as the Data Controller, while the hosting and email service providers act as Data Processors. Your personal data in this scenario would include your IP address while browsing the website and the email address you submitted via the contact form.
Personal data can be different types of data, but they must all relate to an identified or identifiable natural person. This means that individual data points may not be personal data, but the combination of individual data points to identify a natural person makes them personal data. To return to the example, this means that an email address such as 12345@example.com may not be personal data, but when combined with the information that this address belongs to John Smith, it becomes personal data for the Data Controller.
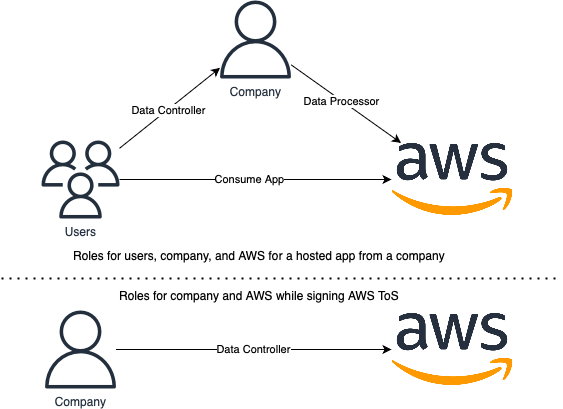
So what are the roles of AWS and the AWS customer, who is the data controller and who is the data processor? Again, we will illustrate this with an example.
As an AWS customer, you want to host an application on AWS that processes personal data. To do so, you must sign a contract with AWS before hosting your application. The information collected when you sign the contract is collected by AWS, so AWS is the data collector in this situation. Once your application is deployed, you are the data collector for the data collected by the application, and AWS is the data processor for hosting and storing your application and related data.
How do you determine who is responsible for what aspect of your hosted application? The Shared Responsibility Model provided by AWS is designed to answer this question. It outlines two distinct responsibilities. AWS itself is responsible for the security of the cloud, but what does that mean? In short, it ensures that the data centres, hardware, and services can be used securely. You, the customer, are responsible for security in the cloud – the secure and compliant use of the cloud services you consume to deliver your application. AWS is responsible for the security of the cloud, which includes updating and operating the hardware, restricting access to and guarding the data centres, and so on.
Now, let’s move on from the abstract responsibilities and roles to the privacy and data protection that you can apply to comply with GDPR.
GDPR Compliance
As stated at the beginning, this blog post focuses on implementing the technical measures to protect your users’ personal data. To give you a comprehensive overview, we will first cover the basic requirements, and then we will go through the seven objectives of data protection and how to implement them to secure your AWS account.
Technology is not the answer to all GDPR requirements, there are also some requirements that need to be addressed at an organisational level. One of the most important is to ensure that you have permission to transfer personal data to AWS. This can be ensured by signing a contract with AWS, which includes the standard contractual clauses (SCCs) provided by the European Union. AWS includes these SCCs in its Data Processing Addendum (DPA), which is part of the Terms and Conditions for using AWS. In addition, AWS is certified under the EU-U.S. Privacy Framework, which permits the export of data to the US, where a similar level of data protection is provided.
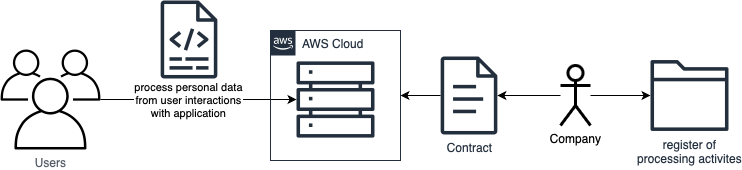
Now that the regulatory issues have been dealt with, let’s focus on the privacy aspects, starting with a general overview of the privacy goals and continuing with the implementation.
- Data minimisation: The goal for data minimisation aims for only collecting and processing the necessary data for a proceeding.
- Availability: It should always be possible to access the personal data for viewing or processing.
- Integrity: There are two different goals for integrity, the integrity of the system and the integrity of the processed data to be intact, complete, correct and up to date.
- Confidentiality: No unauthorised internal or external access to a company’s personal data.
- Non-linking: Data from different proceedings should not be linked together.
- Transparency: It must be identifiable for the service provider, the supervisory authority, and user, for which reason, when, and where data is processed and who is responsible for the processing.
- Intervenability: The requirement that the data subjects are granted their rights to notification, information, rectification, erasure, restriction, data portability, objection and intervention in automated individual decisions without delay.
Next, we dive into how to implement some of the measures with AWS.
Confidentiality
Keeping your data secure is one of the most important things you can do. It must be protected not only from attackers, but also from unauthorised access by employees and the platform or provider.
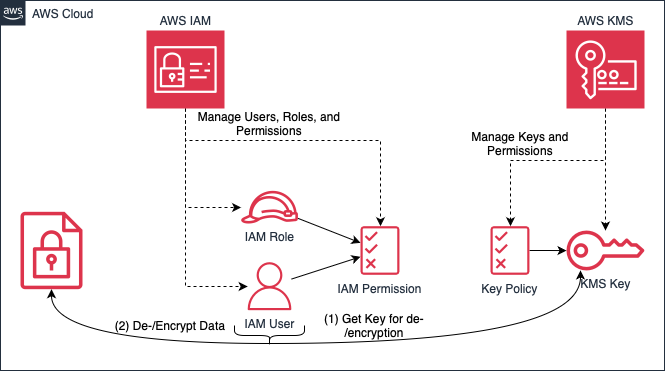
AWS offers two essential services to help keep your data secure: AWS Identity and Access Management (IAM) and AWS Key Management Service (KMS). IAM can be used to manage who can access what, which means you can manage permissions for users and resources. KMS can be used to create, store, and manage key material, as well as securely encrypting and decrypting your data.
In short, to keep your data confidential, you should use encryption wherever possible. To do this, you should implement a policy for managing encryption and key material. In addition, you should follow the principle of “Least Privilege” and limit the permissions granted to your users and resources to the minimum necessary to prevent unauthorised access. You can combine both services: with KMS you can limit who has access to your keys, and with IAM you can define who has access to KMS.
Integrity
Protecting your data from unauthorised access is one thing. It is also important to ensure that the data has not been changed and is correct. Not only should the data be checked for integrity, but the systems that process the data should also be checked for integrity.
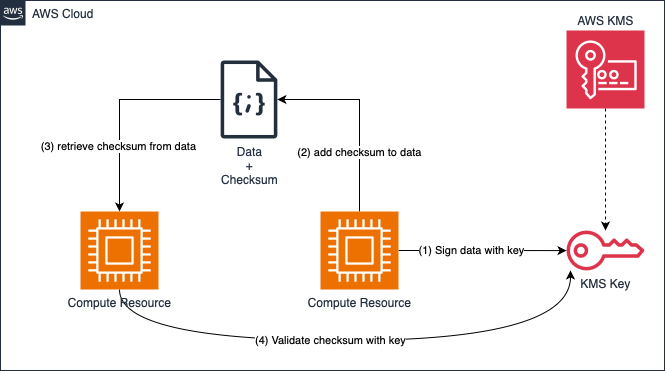
By using different AWS services, you can ensure that your data and the systems processing the data remain as expected. Two ways to do this are to use checksums to validate that the data being processed has not been changed in an unexpected way, and to continuously monitor your environment for changes.
AWS KMS was introduced in the Confidentiality section and can also be used to perform asymmetric cryptographic actions such as creating signatures and validating signatures on your data.
To ensure that your system has not been modified in an unexpected way, you can use AWS Config, a service that continuously evaluates your environment and changes to your resources. When AWS Config detects a change that does not conform to its ruleset, it can trigger various actions, ranging from a simple notification to reverting or even removing the affected non-compliant resource.
Availability
One of the requirements of GDPR is to ensure the availability of personal data.
With AWS, you can achieve this with different and combinable approaches, keeping the data available and the system processing the data available. To unpack this, let’s start by discussing how you can ensure the availability of your data within AWS.
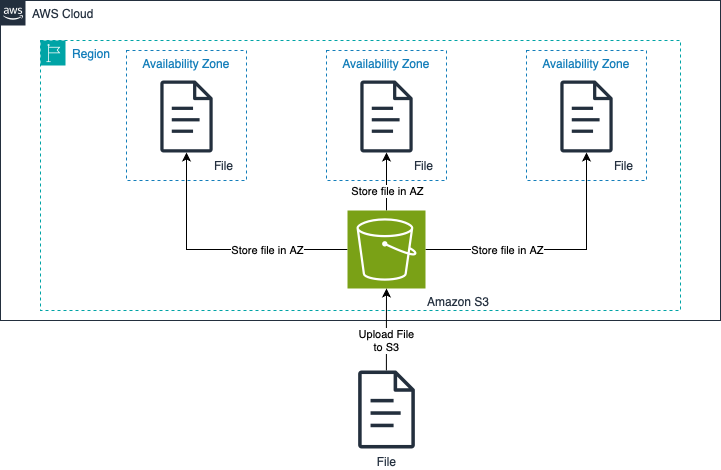
In general, AWS allows you as a customer to store your data in different regions and in different data centres within a region to ensure high availability. AWS provides services to make this as easy as possible, for example, by allowing you to move your backups to another region for disaster recovery if an entire region goes down. Another solution is Amazon Simple Storage Service (S3), a service for storing any data and accessing it securely over the Internet or from within AWS. S3 offers different storage tiers with different levels of redundancy and latency. At the S3 Standard tier, your data is stored in at least three data centres in the same region, without you having to do a thing.
As you can see, AWS makes it easy to store your data securely across multiple data centres. In addition, you can and should combine the storage of your data using encryption and the principles of least privilege that we discussed in the Confidentiality section.
Data Retention and Erasure
Having covered the basics, let’s look at the quality of life services that AWS offers to simplify day-to-day operations, such as ensuring that unused data is deleted.
I want to highlight two different types of data, data stored in logs and data stored in S3. Managing the lifecycle of data in logs is easy with Amazon CloudWatch, a service for monitoring resources and managing log data. Within CloudWatch, you can define policies that automatically delete old logs, while keeping your logs secure from unauthorised use and retrievable using a structured language.
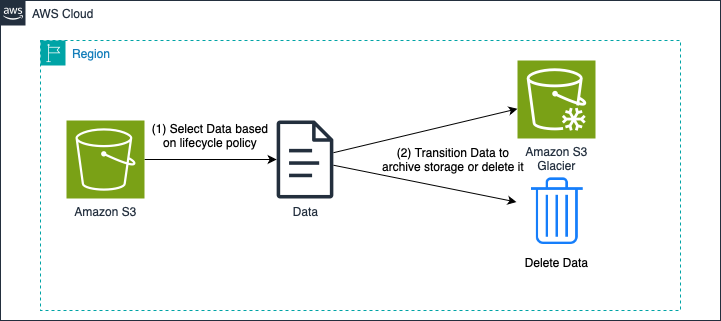
Automatic data deletion is also possible with S3, and you can implement even more complex lifecycle policies. For example, you can configure S3 to delete certain data after a certain period of time, while moving other data to storage classes optimized for archiving because you need to keep it longer for regulatory reasons.
Breach Detection and Notification
We have already discussed how to secure your data and how to ensure that no unexpected changes happen, next let’s dive into detecting a compromised system. entities to notify the authorities of a data breach within 72 hours. Again, AWS offers a number of services to help detect and document security issues.
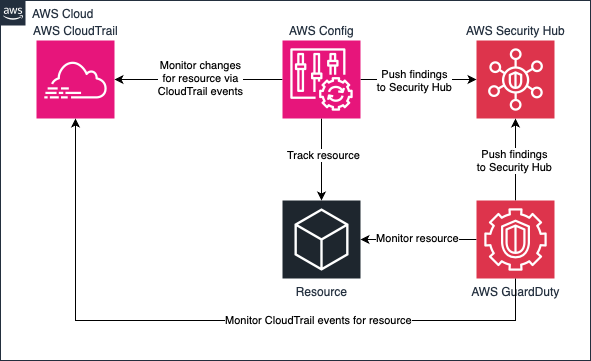
One such service is Amazon GuardDuty. GuardDuty continuously monitors your environment for threats, such as potentially malicious activity or suspicious network traffic. It also integrates seamlessly with a second security service, AWS Security Hub, which is used to document and manage security findings. Security Hub gives you a comprehensive view of security issues across your resources. You can review the issue, check which resource is affected, and close the issue once it has been mitigated.
Another service you can use is AWS Config, which provides continuous monitoring of your environment and the ability to add your own checks or apply a set of best practices, making it easy to catch problems. AWS Config is also able to forward findings to the Security Hub for review.
Conclusion
We now know that AWS can be used in a GDPR-compliant manner, both from an organisational and technological perspective. The organisational requirements for using AWS are met by Amazon and AWS being certified by the EU-US Privacy Framework, and by the implementation of the SCCs in the AWS DPA.
The technical requirements and measures were also discussed. It was shown that by using multiple AWS services, you can safely store and process personal data. It is recommended that you establish policies for the use of encryption and lifecycle management for IAM users and resources.
If you’d like to learn more about implementing encryption with AWS KMS or how to review your IAM resources to enforce the principle of least privilege, feel free to contact us – our AWS experts are here to help.
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More Information