LLMNR Poisoning
Understanding and Mitigating a Critical Network Security Vulnerability
LLMNR Default Windows settings hide a silent credential theft risk called LLMNR poisoning – here’s how to find and eliminate it.
Network security in enterprise environments requires constant vigilance against evolving threats. Among these threats, LLMNR poisoning represents a particularly dangerous attack vector that continues to compromise Windows-based networks. Despite being well-documented, this vulnerability remains exploitable in many organizations due to default configurations and a lack of awareness.
This article examines LLMNR poisoning in depth, providing IT professionals and security teams with the knowledge needed to identify, understand, and remediate this common vulnerability.
Understanding LLMNR and Its Security Implications
Microsoft developed Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) to provide name resolution when DNS fails. These protocols enhance the user experience by offering fallback name resolution mechanisms in Windows environments.
When a DNS lookup fails, Windows systems automatically broadcast an LLMNR or NBT-NS query to the local network, essentially asking: “Who has this hostname I’m looking for?”
The fundamental security issue lies in the protocol design: these broadcast queries can be answered by any device on the network, with no authentication mechanism to verify the legitimacy of responders. This architectural weakness creates the perfect opportunity for attackers to exploit the trust relationship between network devices.
The LLMNR Poisoning Attack Mechanism
LLMNR poisoning follows a straightforward technical flow that exploits this architectural weakness:
Attack Execution Process
- DNS resolution failure: A network user attempts to access a resource with a name that cannot be resolved through DNS. This often occurs due to:
- Typographical errors in resource names
- Temporary unavailability of legitimate resources
- Misconfigured network shares or mappings
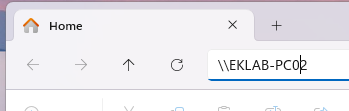
- Broadcast query generation: The Windows system generates an LLMNR or NBT-NS broadcast query to resolve the name
- Malicious response: An attacker monitoring network traffic responds to this broadcast, claiming to be the requested resource
- Authentication attempt: The victim’s system attempts to authenticate to what it believes is the legitimate resource, sending authentication credentials (typically NTLMv2 hashes)
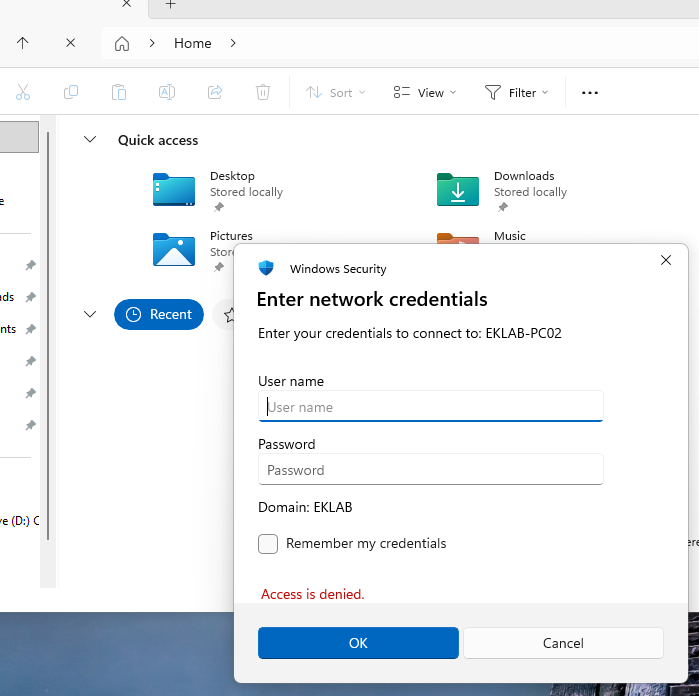
- Credential capture: The attacker captures these authentication credentials for later use Popular penetration testing tools like Responder have automated this process, making it accessible even to less sophisticated threat actors.
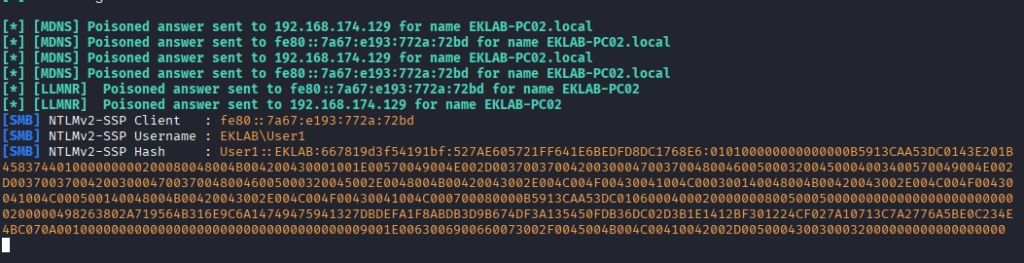
- Credential cracking:
Technical Prerequisites for the Attack
- Default system configurations: both LLMNR and NBT-NS enabled in Windows environments
- Protocol design limitations: The absence of response authentication mechanisms
- Network architecture: Flat networks that allow broadcast traffic across large segments
- User behavior patterns: Common typos and accessing temporarily unavailable resources
Security Impact Analysis
The consequences of successful LLMNR poisoning extend well beyond initial credential capture. Understanding these potential impacts is crucial for proper risk assessment.
Primary Security Impacts
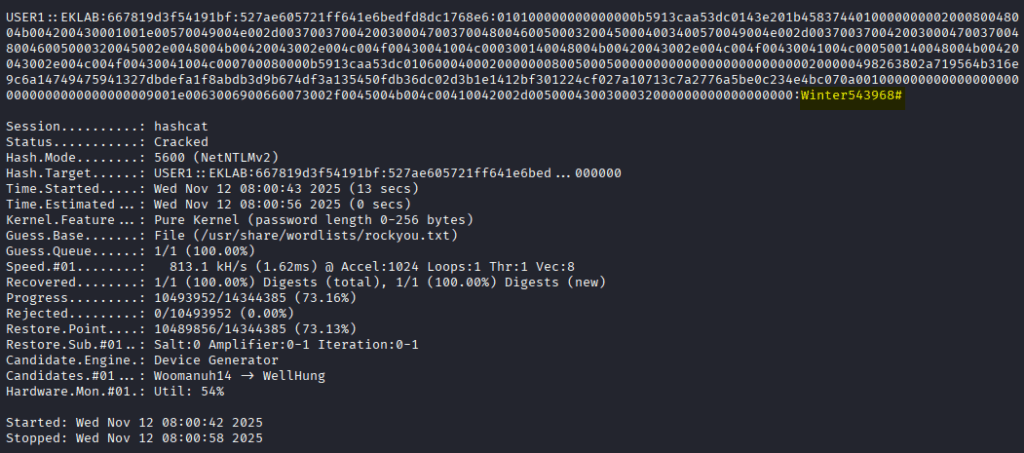
- Credential compromise: attackers capture NTLM hashes and can often crack them offline with tools like Hashcat to reveal clear-text passwords.
- Network visibility: Attackers gain visibility into naming conventions and resource requests, providing valuable reconnaissance information
- Man-in-the-middle position: By positioning themselves between users and requested resources, attackers can intercept, inspect, and potentially modify network traffic in transit
Advanced Attack Progression
- Lateral movement: Using compromised credentials to authenticate to additional systems within the network
- Privilege escalation: Identifying and compromising accounts with elevated privileges to increase network access
- Data exfiltration: Accessing sensitive information using compromised credentials
- SMB relay attacks: Using captured authentication attempts in real-time to authenticate to other systems without needing to crack password hashes
The stealth nature of this attack compounds its danger—without specific monitoring, most organizations remain unaware of active LLMNR poisoning until broader compromise is detected.
Technical Mitigation Strategies
Fortunately, robust mitigation strategies exist for LLMNR/NBT-NS poisoning. These approaches can be implemented through policy enforcement, system configuration, and network architecture changes.
At evoila, we regularly support enterprise customers in identifying and mitigating network protocol vulnerabilities like LLMNR and NBT-NS. Our security assessments often uncover these overlooked configurations that can easily be corrected through proper policy management and network design.
Primary Mitigation: Protocol Disablement
The most effective mitigation is to disable the vulnerable protocols entirely:
Disabling LLMNR via Group Policy
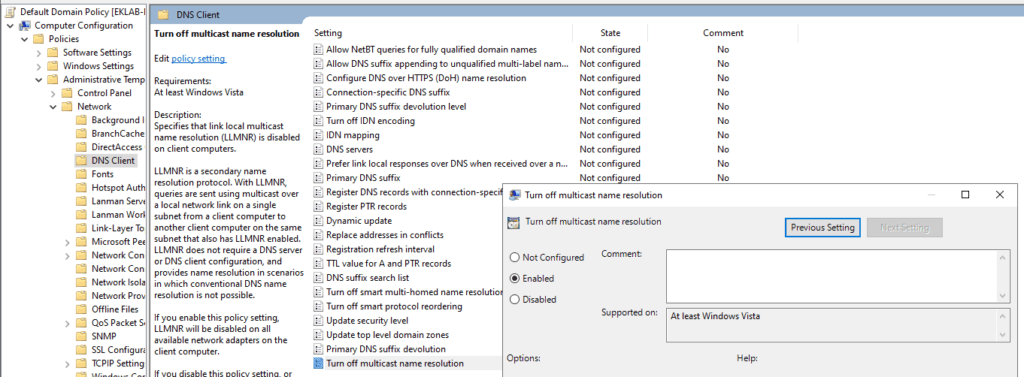
- Access Group Policy Management Console
- Create or edit an appropriate GPO
- Navigate to: Computer Configuration → Administrative Templates → Network → DNS Client
- Enable the setting “Turn off multicast name resolution”
- Apply the GPO to appropriate OUs in your domain
How to Disable NBT-NS via Group Policy (Preferred Enterprise Method)
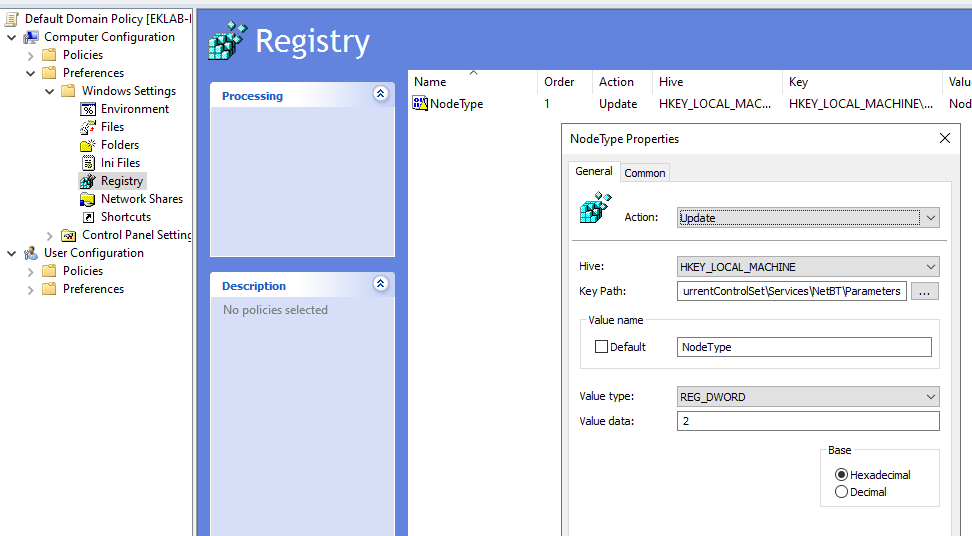
Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NetBT\Parameters
Value: NodeType
Type: REG_DWORD
Data: 2
Disabling NBT-NS on Individual Systems
- Access network adapter properties
- Select “Internet Protocol Version 4 (TCP/IPv4)” → Properties → Advanced → WINS tab
- Select “Disable NetBIOS over TCP/IP”
PowerShell Approach for NBT-NS Disablement
# Requires administrative privileges
Get-NetAdapter | ForEach-Object {
Set-NetAdapterBinding -Name $_.Name -ComponentID 'ms_netbios' -Enabled $false
}Supplementary Security Controls
For comprehensive protection, implement these additional measures:
- SMB signing: Enable SMB signing to prevent relay attacks
- Group Policy: Computer Configuration → Windows Settings → Security Settings → Local Policies → Security Options → “Microsoft network server: Digitally sign communications (always)”
- Network segmentation: Implement proper network segmentation to limit broadcast domains
- Comprehensive DNS management: Ensure all legitimate resources have proper DNS entries
- Security monitoring: Deploy detection mechanisms for LLMNR/NBT-NS poisoning attempts
- 802.1X authentication: Implement port-based network access control
- Local Administrator Password Solution (LAPS): Deploy Microsoft LAPS to manage local administrative passwords
Detection and Testing Methods
Security teams should implement both detection mechanisms and regular testing to ensure protection against LLMNR poisoning attacks.
Detection Implementation
Deploy these monitoring solutions to identify potential LLMNR poisoning attempts:
- Network traffic analysis: Configure Wireshark or network monitoring tools with these filters:
- LLMNR traffic:
udp port 5355 - NBT-NS traffic:
udp port 137
- LLMNR traffic:
- SIEM integration: Configure alerts for:
- Unusual volume of LLMNR/NBT-NS queries
- Multiple failed authentication attempts following name resolution
- Responses to LLMNR/NBT-NS queries from unauthorized systems
- Elasticsearch/ELK Stack Detection: For organizations using Elasticsearch for log analysis, the following query can detect potential LLMNR poisoning attempts:
{
"query": {
"bool": {
"must": [
{
"terms": {
"destination.port": [5355, 137]
}
},
{
"term": {
"network.protocol": "udp"
}
}
],
"should": [
{
"match": {
"dns.question.name": "*"
}
},
{
"exists": {
"field": "netbios.name"
}
}
]
}
},
"aggs": {
"source_ips": {
"terms": {
"field": "source.ip",
"size": 10
}
},
"destination_ips": {
"terms": {
"field": "destination.ip",
"size": 10
}
}
}
}
This query identifies UDP traffic on LLMNR (port 5355) and NBT-NS (port 137) and aggregates by source and destination IPs to identify potential poisoning sources.
- Windows Event Monitoring: Look for event IDs related to authentication failures following name resolution attempts
Security Testing Procedures
Security teams should regularly test their defenses against LLMNR poisoning. The following tools are commonly used:
- Responder: The industry-standard tool for LLMNR/NBT-NS poisoning testing
- Regular execution in audit mode can identify vulnerable systems
- Command format:
python Responder.py -I <interface> -A
- Inveigh: PowerShell-based alternative for Windows environments
- Particularly useful in environments where Python-based tools are restricted
- Command format:
Import-Module .\Inveigh.ps1; Invoke-Inveigh -ConsoleOutput Y
- Metasploit: Offers auxiliary modules for LLMNR poisoning
Conduct testing only with proper authorization and in controlled environments to avoid disrupting production services.
At evoila, we also perform professional penetration tests to help organizations detect and remediate such vulnerabilities as part of a comprehensive network security strategy.
Conclusion and Recommendations
LLMNR poisoning represents a persistent security risk in Windows environments that continues to be exploited by threat actors. The vulnerability stems from default configuration settings rather than software defects, making it particularly dangerous as it exists “by design” in many networks.
Key Takeaways
- Risk assessment: LLMNR poisoning should be included in all internal network security assessments
- Protocol management: Default Windows name resolution protocols should be disabled where not explicitly required
- Defense in depth: Multiple mitigation strategies should be deployed simultaneously
- Regular testing: Security teams should conduct periodic testing for this vulnerability
- Employee awareness: Technical staff should understand this vulnerability and its implications
Implementation Strategy
Organizations should approach LLMNR poisoning mitigation as part of a broader security hardening process:
- Inventory: Identify all Windows systems in the environment
- Testing: Conduct preliminary testing to identify vulnerable systems
- Planning: Develop a staged rollout plan for mitigation controls
- Deployment: Implement GPOs in phases, starting with test environments
- Verification: Conduct post-implementation testing to confirm effectiveness
- Monitoring: Deploy ongoing detection capabilities
While disabling LLMNR and NBT-NS might create occasional user inconvenience in poorly configured environments, the security benefits significantly outweigh these potential issues. Organizations should prioritize proper DNS configuration to eliminate dependency on these fallback protocols.
Organizations that implement the technical controls outlined in this article can eliminate an entire class of network attacks that still target unprotected environments.
Protect your organization before attackers exploit these weaknesses.
Get in touch with the evoila security team to assess your current network configuration and implement tailored safeguards against credential theft and lateral movement.
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More Information